Programs and Processes in Linux - 2
What Happens When You Run sudo ls?
When you run sudo ls, the process creation sequence introduces an additional layer due to the role of sudo in handling privilege escalation. This also involves modifications to the environment variables to ensure security.
1. Shell Forks a Child Process for sudo
When you type
sudo lsand press Enter, the shell (e.g.,bash) creates a new child process using thefork()system call.The child process inherits:
The parent shell's environment variables.
Open file descriptors (e.g., stdin, stdout, stderr).
Permissions (UID and GID of the user running the shell).
After forking, the child process replaces its code with the
sudobinary using theexecve()system call. This means:The child process is now running the
sudoprogram.The parent shell process waits for the
sudoprocess to complete.
2. sudo Modifies the Environment
Before executing the
lscommand,sudomakes significant changes to the environment variables to prevent privilege escalation attacks. This ensures a secure execution context.
What Changes Does sudo Make?
Environment Variables Cleared:
Most environment variables inherited from the shell are cleared. This includes variables like
$LD_PRELOADor$LD_LIBRARY_PATH, which could be exploited to inject malicious libraries.
Essential Variables Retained:
A minimal set of variables is retained for compatibility:
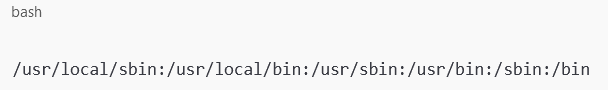
$TERM: Maintains terminal settings.$HOME: Often set to/rootfor the root user.$PATH: Adjusted to include directories like/sbinand/usr/sbin, which are required for root-only commands.
Example of modified
$PATH:
Optional Behavior:
If you run
sudowith the-Eflag (sudo -E ls), it preserves the parent shell's environment variables without clearing them. This can be useful but potentially insecure.
At this stage, the modified environment is prepared, and
sudomoves to execute the next process.
3. sudo Forks Another Child Process for ls
After verifying your credentials (via cached credentials or a password prompt),
sudoforks another child process.The new child process inherits the sanitized environment prepared by
sudo.The child’s privileges are elevated to root:
UID is set to
0(root user).GID is set to
0(root group).
The child process replaces its code with the
lsbinary using theexecve()system call, inheriting the adjusted environment and root-level permissions.
4. The ls Process Executes
The
lsprocess now executes with elevated privileges:It runs with the environment prepared by
sudo, allowing it to access files and directories restricted to regular users.Example: Listing files in
/root, which would be inaccessible without root privileges.
Once
lscompletes its execution:It sends an exit signal to the
sudoprocess.The
sudoprocess terminates, passing control back to the original shell process.
Key Takeaways About Environment Changes
Default Behavior:
sudosanitizes the environment by clearing potentially dangerous variables and retaining only essential ones for security.
Customizing Behavior:
Use the
-Eflag to retain the parent shell's environment when running commands withsudo.Define environment variables to keep using the
env_keepdirective in the/etc/sudoersfile.
Security Implications:
Clearing the environment helps prevent privilege escalation attacks where malicious code could be injected via variables like
$LD_PRELOAD.
Revised Process Hierarchy
Here’s the updated process flow with environment changes highlighted:
This careful orchestration by the shell,
sudo, and the kernel highlights Linux’s robust approach to process management and security. Understanding these details provides clarity on how Linux balances functionality with protection.